Cybersecurity in a Digital Age Securing your online presence is crucial in today’s digital age
Cybersecurity plays a pivotal role in safeguarding sensitive information and preventing unauthorized access.
In this article, we’ll explore key aspects of cybersecurity to help you protect your online presence.
- 1 Understanding Cybersecurity: Cybersecurity in a Digital Age
- 1.1 1. Strong Passwords:
- 1.2 2. Two-Factor Authentication (2FA):
- 1.3 3. Regular Software Updates:
- 1.4 4. Secure Wi-Fi Networks:
- 1.5 Protecting Personal Information: Cybersecurity in a Digital Age
- 1.6 1. Be Cautious with Personal Information:
- 1.7 2. Phishing Awareness:
- 1.8 Business and Work Considerations: Cybersecurity in a Digital Age
- 1.9 1. Secure Communication Channels:
- 1.10 2. Employee Training:
- 1.11 3. Data Backups:
- 1.12 Monitoring and Vigilance: Cybersecurity in a Digital Age
- 1.13 1. Monitor Account Activity:
- 1.14 2. Use Security Software:
- 1.15 Conclusion: Cybersecurity in a Digital Age
- 1.16 Frequently Asked Questions (FAQ) on Cybersecurity: Cybersecurity in a Digital Age
- 1.17 1. What is Cybersecurity?
- 1.18 2. Why is Cybersecurity Important?
- 1.19 3. How Can I Create a Strong Password?
- 1.20 4. What is Two-Factor Authentication (2FA)?
- 1.21 5. How Can I Recognize Phishing Attempts?
- 1.22 6. Why Should I Keep Software Updated?
- 1.23 7. What Steps Can I Take to Secure my Wi-Fi Network?
- 1.24 8. How Can Businesses Enhance Cybersecurity?
- 1.25 9. Why is Phishing Awareness Important?
- 1.26 10. How Often Should I Back Up my Data?
- 1.27 11. What Should I Do if I Notice Suspicious Account Activity?
Understanding Cybersecurity: Cybersecurity in a Digital Age
1. Strong Passwords:
Start by creating strong, unique passwords for each online account. Use a combination of upper and lower-case letters, numbers, and special characters. Avoid easily guessable information, such as birthdays or names.
2. Two-Factor Authentication (2FA):
Enable 2FA whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your mobile device, in addition to your password.
3. Regular Software Updates:
Keep your operating system, antivirus software, and applications up to date. Software updates often include security patches that address vulnerabilities, helping protect against cyber threats.
4. Secure Wi-Fi Networks:
Ensure your home Wi-Fi network is secured with a strong password. Use WPA3 encryption if available. Avoid using default router login credentials, and change them to something unique.
Protecting Personal Information: Cybersecurity in a Digital Age
1. Be Cautious with Personal Information:
Avoid sharing sensitive information, such as your full address, phone number, or financial details, on public platforms. Be mindful of what you share on social media and adjust privacy settings accordingly.
2. Phishing Awareness:
Be cautious of phishing attempts. Avoid clicking on suspicious links in emails or messages. Verify the authenticity of requests for personal information, especially if they seem unusual or urgent.
Business and Work Considerations: Cybersecurity in a Digital Age
1. Secure Communication Channels:
When conducting business online, use secure communication channels. Ensure that emails and messages containing sensitive information are encrypted.
2. Employee Training:
If you’re a business owner, invest in cybersecurity training for your employees. Educate them on recognizing and avoiding potential threats like phishing attacks.
3. Data Backups:
Regular Backups: Regularly back up your important data. This ensures that even if you experience a cybersecurity incident, you can recover your information. Use secure, encrypted backup solutions.
Monitoring and Vigilance: Cybersecurity in a Digital Age
1. Monitor Account Activity:
Regularly review your online accounts for any suspicious activity. Many platforms offer account activity logs that allow you to track logins and actions performed on your account.
2. Use Security Software:
Install reputable antivirus and anti-malware software on your devices. Keep the software updated to protect against the latest threats.
Conclusion: Cybersecurity in a Digital Age
In an era where our lives are increasingly interconnected online, cybersecurity is paramount. By implementing these practices, you can significantly reduce the risk of falling victim to cyber threats. Stay vigilant, educate yourself, and prioritize the protection of your digital identity and sensitive information. Remember, proactive measures today can prevent potential cybersecurity challenges in the future.
Frequently Asked Questions (FAQ) on Cybersecurity: Cybersecurity in a Digital Age
1. What is Cybersecurity?
Answer: Cybersecurity involves the practice of protecting systems, networks, and data from digital attacks. It encompasses measures to ensure confidentiality, integrity, and availability of information in the digital space.
2. Why is Cybersecurity Important?
Answer: Cybersecurity is crucial to safeguard personal and sensitive information, prevent unauthorized access, and protect against cyber threats such as hacking, identity theft, and data breaches.
3. How Can I Create a Strong Password?
Answer: Create a strong password by using a mix of upper and lower-case letters, numbers, and special characters. Avoid easily guessable information like birthdays or names. Consider using a passphrase for added security.
4. What is Two-Factor Authentication (2FA)?
Answer: Two-Factor Authentication adds an extra layer of security by requiring a second form of verification, typically a code sent to your mobile device, in addition to your password.
5. How Can I Recognize Phishing Attempts?
Answer: Be cautious of unsolicited emails or messages, especially those requesting personal information. Check for spelling errors or unusual sender addresses. Avoid clicking on suspicious links and verify requests for sensitive information.
6. Why Should I Keep Software Updated?
Answer: Software updates often include security patches that address vulnerabilities. Keeping your operating system, antivirus software, and applications updated reduces the risk of exploitation by cyber attackers.
7. What Steps Can I Take to Secure my Wi-Fi Network?
Answer: Secure your Wi-Fi network by using a strong, unique password. Enable WPA3 encryption if available. Avoid using default router login credentials, and change them to something unique.
8. How Can Businesses Enhance Cybersecurity?
Answer: Businesses can enhance cybersecurity by providing employee training on security best practices, securing communication channels, regularly updating software, and implementing secure data backup solutions.
9. Why is Phishing Awareness Important?
Answer: Phishing is a common tactic used by cybercriminals. Being aware of phishing attempts helps individuals and businesses avoid falling victim to deceptive schemes that could compromise sensitive information.
10. How Often Should I Back Up my Data?
Regularly back up your important data, and the frequency may depend on your usage. Consider automated backup solutions and ensure that the backups are stored securely, preferably in encrypted form.
11. What Should I Do if I Notice Suspicious Account Activity?
If you notice suspicious account activity, change your passwords immediately, enable 2FA if not already enabled, and contact the platform's support for assistance. Regularly monitor your accounts for any unusual actions.
Remember, staying informed and implementing cybersecurity best practices is essential in maintaining a secure online presence.
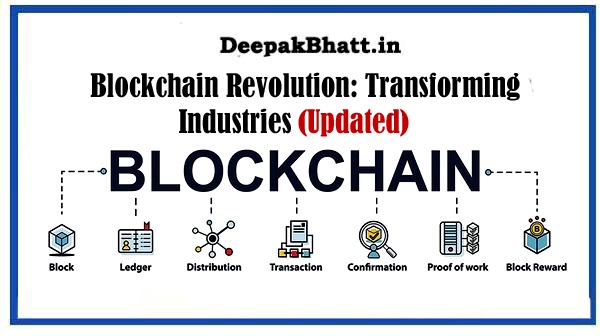
Blockchain Revolution: Complete Transforming Industries
5G Technology: Power of Connectivity
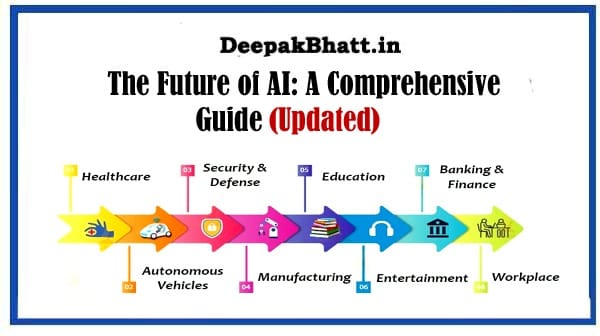
The Future of AI: A Comprehensive Guide
Navigating Number Systems: Converting Octal to Decimal with Ease